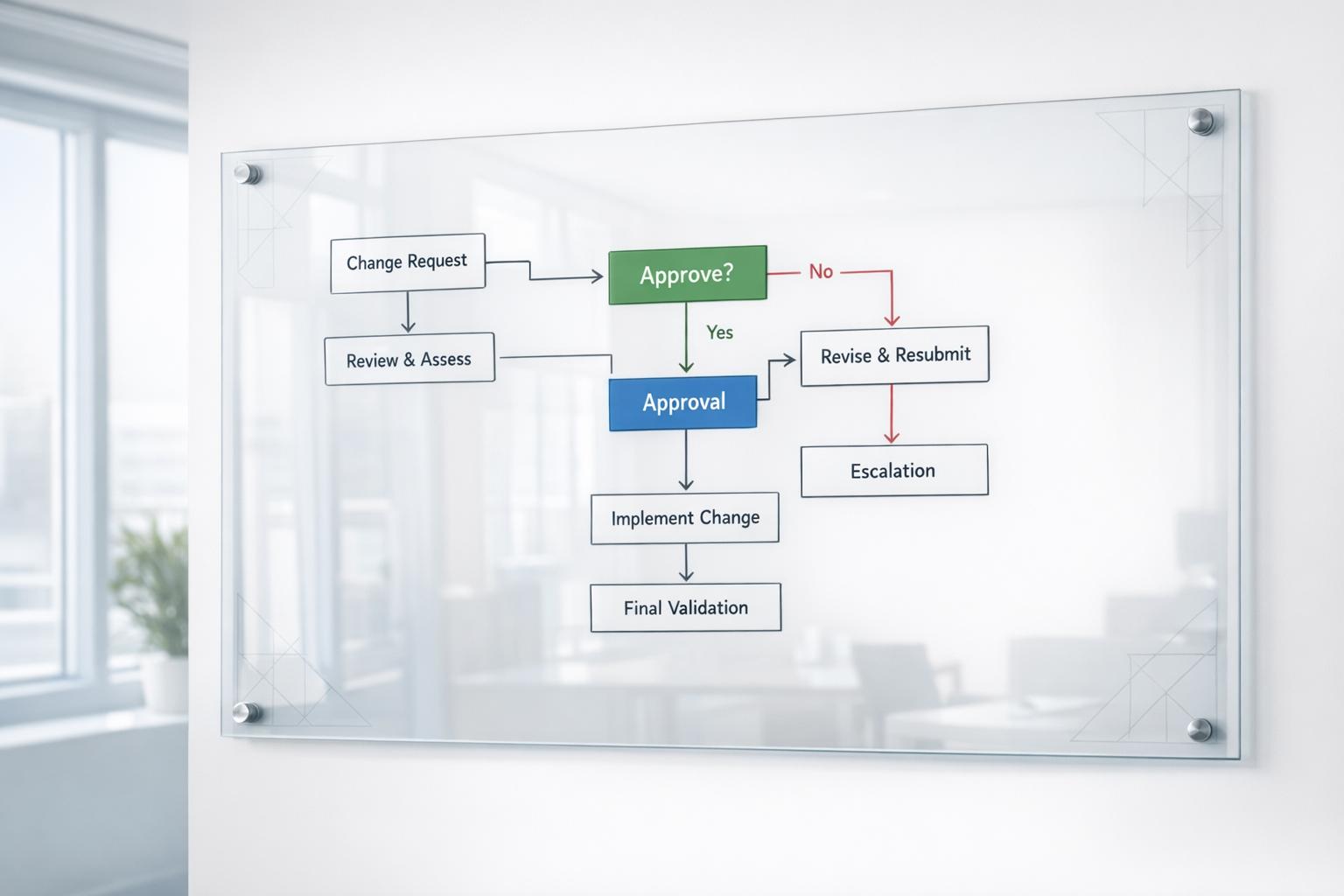
Wireless access points are a critical part of modern networks, but they can also be a weak link if not secured properly. Here's what you need to know:
- Change Default Settings: Update default SSIDs, passwords, and admin credentials to prevent easy access by attackers.
- Use Strong Encryption: Enable WPA3 (or WPA2 with AES if WPA3 isn't available) to secure data transmission.
- Regular Firmware Updates: Keep your devices updated to patch vulnerabilities and enable new security features.
- Physical Security: Restrict physical access to devices and secure them in locked areas.
- Network Segmentation: Use VLANs to isolate traffic and reduce the impact of potential breaches.
- Monitor Activity: Regularly review logs, scan for rogue devices, and deploy intrusion detection systems.
- Employee Training: Educate staff on identifying and reporting wireless security risks.
- Secure Device Disposal: Properly erase or destroy decommissioned hardware to prevent data leaks.
Wireless access point security isn't just about technology - it requires regular maintenance, monitoring, and proactive measures to minimize risks. By implementing these practices, you can protect sensitive data, maintain compliance, and keep your network safe.
CORPORATE WI-FI SECURITY: Wireless Network Best Practices for Businesses
Change Default Settings and Passwords
Wireless access points often come with factory settings that are widely known and easily accessible. Manufacturers make default usernames, passwords, and network names available in user manuals and online databases, leaving these devices vulnerable to attackers using automated tools to scan for networks running on default configurations. A 2022 survey found that over 60% of small businesses had never updated the default passwords on their wireless routers, putting them at significant risk of breaches. In fact, automated tools can compromise networks using factory settings in under 10 minutes.
Leaving default settings in place creates multiple security gaps. Beyond weak passwords, unchanged configurations can expose SNMP community strings, encryption keys, and management interfaces. Attackers often exploit these vulnerabilities using publicly available credential lists. To protect your network, start by updating your SSID and password to disrupt these automated threats.
Update Default SSID and Passwords
Your SSID (Service Set Identifier) is the name your network broadcasts to nearby devices. Default SSIDs like "Linksys", "NETGEAR", or "TP-Link_5G" give attackers a clear idea of the equipment you're using, making it easier for them to select the right exploits.
Choose a unique SSID that doesn’t reveal your organization’s name, location, or equipment type. For example, instead of using "AcmeCorp_WiFi" or "Linksys123", opt for something less predictable, like "AP-7x9Q2" or "Network_Delta." This simple adjustment makes it harder for attackers to identify your network or deploy pre-built attack scripts.
Next, replace the default network password with a strong passphrase. A secure password should have at least 12 characters and include a mix of uppercase and lowercase letters, numbers, and special symbols. Avoid using dictionary words, company names, or any personal information that attackers might guess.
Don’t overlook vendor-provided encryption keys and other default security settings. These also need to be updated to close potential entry points for attackers. Once your SSID and passwords are secure, focus on locking down administrative access.
Use Strong Admin Passwords and Rotate Them Regularly
Administrative access to your wireless access points gives complete control over your network. If attackers gain access, they can redirect traffic, steal sensitive data, or create backdoors for future breaches.
To prevent this, use strong admin passwords and a regular rotation schedule. Update passwords and shared keys every 90 days, or immediately after staff changes or suspected breaches. Regular updates reduce the risk of long-term credential theft and limit potential damage if a password is compromised.
When creating admin passwords, follow the same complexity guidelines as network passwords but make them even longer and more secure. Using passphrases that combine random words, numbers, and symbols can make them both strong and easier for authorized users to remember.
Update passwords immediately when employees leave or change roles. Former employees can pose insider threats, and delays in updating credentials can leave your network vulnerable for weeks or months. Use encrypted password managers or secure systems to track changes and maintain an audit trail. For businesses managing multiple access points, tools like BizBot (https://bizbot.com) can simplify credential management and help ensure consistent security practices.
Additionally, change default SNMP community strings if SNMP is enabled, disable unused management interfaces, and turn off remote administration unless absolutely necessary.
| Setting | Default Risk | Recommended Action |
|---|---|---|
| SSID | Publicly known | Change to a unique identifier |
| Admin Password | Easily guessed | Set a strong, complex password |
| Encryption Key | Publicly known | Use a unique, strong key |
| SNMP Community String | Publicly known | Use a complex string, enable SNMPv3 |
| Shared Keys | Publicly known | Rotate every 90 days |
Taking the time to change default settings significantly improves your network's security. This step eliminates common vulnerabilities, reduces exposure to automated attacks, and sets the stage for more advanced protections. By doing so, you make your network far less attractive to attackers, forcing them to put in considerable effort to breach it.
Set Up Strong Encryption and Authentication
Encryption and authentication are essential for protecting data during transmission and ensuring that only authorized users can access your network. Without these safeguards, sensitive information like passwords and financial details can be intercepted by attackers. In fact, Verizon's 2023 Data Breach Investigations Report found that 18% of breaches in the US involved compromised wireless access points or weak Wi-Fi security settings.
Modern encryption protocols, when configured correctly, provide robust protection for your data. Let’s explore how to set up encryption and authentication to secure your communications effectively.
Use WPA2 or WPA3 for Encryption
WPA3 is currently the most secure option, offering 192-bit encryption keys compared to WPA2's 128-bit keys. It also includes features like Simultaneous Authentication of Equals (SAE), which defends against brute-force attacks, and forward secrecy, ensuring that past communications remain secure even if your network password is compromised.
As of 2023, more than 60% of new enterprise Wi-Fi deployments in the US use WPA3, a significant increase from 35% in 2021. To implement WPA3 - or WPA2 if WPA3 isn’t supported - log into your wireless access point's management interface, navigate to the security settings, and select WPA3 as the security mode. If WPA3 isn’t available, choose WPA2 and ensure the encryption method is set to AES (Advanced Encryption Standard) instead of the outdated TKIP protocol.
For organizations transitioning to WPA3, enabling a mixed mode (WPA2/WPA3) allows both types of devices to connect during the migration period. Once all devices are WPA3-compatible, phase out WPA2 to ensure maximum security.
Configure Enterprise Authentication Protocols
While pre-shared keys might be sufficient for small networks, enterprise environments require more advanced solutions. Implementing 802.1X with the Extensible Authentication Protocol (EAP) ensures stronger security by authenticating individual users rather than just devices. This method also simplifies managing network access and revoking permissions when employees leave. For even stronger authentication, EAP-TLS uses digital certificates.
To set up 802.1X, use a RADIUS server and configure your access points for WPA2-Enterprise or WPA3-Enterprise mode with the appropriate EAP method. If you opt for certificate-based authentication, distribute digital certificates to client devices and test the setup to ensure only authorized users can connect.
Smaller organizations can use cloud-based authentication services to achieve enterprise-level security without the complexity of managing a RADIUS server. These services often integrate seamlessly with existing directory systems, streamlining IT operations and security policies. Once enterprise authentication is configured, disable outdated protocols to eliminate potential vulnerabilities.
Disable Outdated Security Standards
Legacy protocols like WEP and the original WPA should be disabled immediately, as they are highly vulnerable to attacks. These outdated protocols can allow attackers to force devices to downgrade to weaker encryption, bypassing your network’s stronger security measures. Leaving them enabled increases the risk of eavesdropping, data theft, and unauthorized access.
To mitigate these risks, access your wireless access point's configuration interface and review the security settings. Look for options labeled "WEP", "WPA (not WPA2)", or "Mixed Mode" that include older standards, and disable them. Ensure that only WPA2 with AES or WPA3 is available. Don’t overlook guest networks - they often default to weaker settings. Apply the same encryption standards to guest access and use network segmentation to isolate guest traffic.
| Protocol | Encryption Strength | Security Status | Recommendation |
|---|---|---|---|
| WEP | 40/104-bit RC4 | Easily cracked in under 1 minute | Disable immediately |
| WPA (original) | TKIP | Multiple known vulnerabilities | Disable completely |
| WPA2 | AES 128-bit | Some vulnerabilities (patched) | Minimum acceptable standard |
| WPA3 | AES up to 192-bit | Current best practice | Recommended for new deployments |
Document your encryption and authentication settings as part of your security policy, and regularly audit your network to ensure no legacy protocols have been re-enabled due to firmware updates or configuration changes. This proactive approach helps maintain a secure environment while supporting your business needs.
Keep Firmware Updated with Security Patches
Once you've secured your access point settings and encryption, the next critical step is keeping your firmware up-to-date. Firmware updates are essential for addressing vulnerabilities that could serve as entry points for attackers. One major risk comes from default configurations and outdated firmware, particularly after a factory reset, which can undo security improvements. According to a 2023 Ponemon Institute study, 57% of organizations faced security incidents caused by unpatched network device vulnerabilities, with an average delay of 38 days to apply patches.
A stark example of this risk is the breach at Baltimore County Public Schools. Unpatched firmware led to exposed sensitive data and a prolonged service outage. This incident highlights the importance of incorporating regular firmware updates into your wireless security strategy.
Schedule Regular Updates
Having a structured update schedule is key to ensuring no device is left vulnerable. For most organizations, monthly or quarterly updates are sufficient, but environments with higher security demands may need more frequent checks.
Maintain a detailed inventory of all access points, including their model, firmware version, location, and the personnel responsible for their maintenance. This inventory acts as a guide, helping you track updates systematically and ensuring no devices are overlooked.
IT teams should also set up alerts for firmware updates. Many manufacturers offer email notifications or RSS feeds for new releases. Enabling these alerts right after deployment ensures updates are applied promptly.
To minimize disruptions, schedule updates during periods of low network activity. If you have redundant access points, they can help maintain service continuity during the update process. Using enterprise wireless management platforms can further simplify this by centralizing device monitoring and automating firmware deployments.
Test and Document Updates
Before rolling out firmware updates across your network, it's crucial to test them in a controlled environment. Use a lab setup that mirrors your production network to ensure the update doesn't cause compatibility issues or disrupt critical functions. Testing should focus on key features like user authentication, network segmentation, and guest access, while also monitoring performance metrics to confirm that connection stability and throughput remain unaffected.
Once testing is complete, document the process thoroughly. Record details such as the device model, firmware version, update date, personnel involved, and any issues encountered. Maintaining these records not only supports internal reviews but also simplifies audits.
Tools like BizBot can help streamline this process by centralizing task scheduling, inventory management, and compliance documentation. These tools make it easier to track updates and ensure you're meeting regulatory requirements.
The National Institute of Standards and Technology (NIST) advises organizations to implement a formal patch management policy that includes testing, deployment, and documentation of firmware updates. Additionally, frameworks like PCI DSS mandate documented patch management processes.
Lastly, firmware updates are often necessary to enable support for stronger encryption standards. If a device's firmware cannot be updated to support modern security protocols like WPA3 or WPA2 with AES, it's time to remove that device from your network. Leaving such devices in place could expose your network to unnecessary risks.
sbb-itb-d1a6c90
Secure Physical Access and Network Segments
Controlling both physical access to your wireless access points and how they connect to your network is crucial. Together, physical security and network segmentation create layers of defense against potential attackers.
Restrict Physical Access to Devices
When someone gains physical access to your wireless access points, they can compromise your network in several ways - resetting devices to factory settings, installing malicious firmware, or stealing sensitive configuration details.
Keep devices in secure, locked areas or tamper-proof enclosures. Place access points in locked network closets, server rooms, or ceiling-mounted enclosures that require authorization for access. Tamper-evident enclosures can help detect unauthorized access during or after business hours.
Maintain detailed records of your devices. Document each access point’s serial number, installation date, location, and assigned personnel in your inventory system. This makes it easier to identify missing or altered devices during security checks.
Perform regular inspections. Schedule quarterly checks to look for signs of tampering, unauthorized devices, or changes in access point placement. Any unusual findings should be investigated immediately, as they could signal a breach or the installation of rogue devices.
For businesses with multiple locations, centralized management tools can simplify tracking and maintenance. Platforms like BizBot offer solutions tailored to help smaller organizations maintain device inventories and meet compliance requirements.
Once physical security is addressed, it’s time to focus on creating logical boundaries within your network to minimize risks.
Set Up VLANs and Network Segmentation
After securing physical access, network segmentation becomes the next layer of defense. By isolating wireless traffic from critical business systems, you limit the potential damage from breaches.
Use VLANs (Virtual Local Area Networks) to separate wireless traffic. Create distinct VLANs for different purposes: one for employees, another for guests, and a third for IoT devices like printers or security cameras. This ensures that, for example, a compromised guest device cannot access sensitive employee or business data.
Implement firewalls to regulate traffic between VLANs and your core network. These firewalls should block unauthorized traffic while allowing only essential services. For instance, employee devices might need access to email servers or shared files, but they shouldn’t connect directly to sensitive databases like customer records or accounting systems.
Consider out-of-band management for added security. Use a dedicated VLAN or a separate network for managing your wireless infrastructure. This isolates management traffic from user data, reducing the chances of attackers compromising your access points.
Review your firewall rules regularly - ideally every quarter. As your business evolves, so do its needs, and your firewall policies should reflect those changes while maintaining strong security.
Smaller businesses can achieve basic segmentation with managed switches and firewalls. Larger organizations might need more advanced setups, including multiple VLANs, enhanced monitoring tools, and specialized security appliances. Regardless of size, segmentation reduces attack surfaces and helps contain incidents if breaches occur.
Focus especially on protecting critical systems. Identify which systems hold sensitive data or are essential to operations, and ensure your wireless networks cannot access these resources without proper authentication and authorization. This approach strengthens your overall security posture and minimizes risks to your most valuable assets.
Monitor Networks and Respond to Security Threats
Keeping a close eye on your wireless network turns it from a potential weak spot into a well-guarded security barrier. Without consistent monitoring, threats can linger unnoticed, creating opportunities for data breaches.
Conduct Regular Network Monitoring
Monitoring your network isn’t just about making sure devices stay connected - it’s about actively searching for potential threats or unusual activity. For example, reviewing wireless audit logs can reveal patterns like repeated failed login attempts or unusual traffic spikes, especially during off-hours, which could signal security concerns.
Automated tools play a big role here, detecting anomalies such as unexpected traffic or authentication failures and sending alerts to your central monitoring system. These tools should seamlessly integrate with your current security setup, offering a unified view of network activity.
Quarterly scans for rogue access points are essential, but don’t rely solely on scheduled checks. Attackers can plant unauthorized access points to steal credentials or create backdoors into your network. Use specialized wireless scanners to hunt for devices broadcasting SSIDs that mimic your legitimate networks - this tactic, known as "evil twin" attacks, is a common method used by hackers.
Maintaining an up-to-date inventory of authorized wireless devices, including their MAC addresses and locations, is another critical step. This inventory simplifies identifying unauthorized devices during scans. Also, document any changes to your wireless setup, such as new access points, configuration updates, or device relocations.
“According to the 2023 Verizon Data Breach Investigations Report, over 40% of breaches involving wireless networks were detected by log review and network monitoring rather than automated alerts alone”.
This finding emphasizes the need for human oversight alongside automated systems.
Store audit logs securely on a centralized server with strict access controls to prevent tampering. Assign specific personnel to review these logs, and establish clear protocols for escalating issues when suspicious activity is detected. Regular log analysis helps you understand your network’s normal behavior, making it easier to spot anything unusual.
Pair proactive monitoring with advanced detection systems to strengthen your network’s defenses.
Deploy Intrusion Detection Systems (IDS)
Wireless intrusion detection systems (IDS) are designed to catch threats early by identifying attack patterns and unusual behaviors associated with wireless vulnerabilities.
To maximize their effectiveness, place IDS sensors strategically. Focus on areas like critical access points, high-traffic zones, and network perimeters where external attacks are more likely. Make sure your sensors monitor all wireless channels in use, not just the primary ones.
Set up alerts for key events, such as new device connections, repeated authentication failures, or suspicious traffic.
“The Ponemon Institute found that organizations with continuous monitoring reduce the average time to detect a breach from 197 days to 70 days”.
This underscores the importance of quick threat detection.
Integrate IDS with your centralized logging and incident response systems to ensure alerts are delivered to the right people without delay. Regularly test your IDS setup through controlled penetration tests to confirm its effectiveness.
Cloud-based IDS solutions are becoming more popular, especially in distributed wireless environments. These systems don’t require extensive on-site infrastructure and often use machine learning to adapt to your network’s normal behavior, improving detection accuracy over time.
By incorporating IDS into your monitoring efforts, you create a stronger, more resilient wireless security framework.
Train Employees on Security Risks
Technology alone isn’t enough - your workforce plays a crucial role in defending against wireless threats. A well-informed team can act as an additional layer of protection. Conduct security awareness training at least twice a year, focusing on the specific risks employees might face in their day-to-day work.
Teach staff to recognize warning signs of wireless attacks, such as unexpected disconnections, requests for credentials from unknown sources, or the sudden appearance of suspicious networks that resemble your legitimate SSIDs. Even small irregularities can indicate a larger issue.
Establish clear reporting procedures for any unusual wireless activity. Employees should know exactly who to contact and what details to provide if they suspect something is wrong.
Use real-world examples during training to show how attacks happen. For instance, attackers might set up rogue access points in parking lots or nearby buildings to steal credentials, or use social engineering to trick employees into connecting to fake networks.
Encourage a culture where employees feel comfortable reporting incidents without fear of blame. If someone accidentally connects to a rogue network or falls for a scam, reporting it quickly can prevent a minor issue from escalating into a major problem.
Tools like BizBot can simplify training documentation and make incident reporting easier. Regular refresher courses help reinforce key concepts and introduce new threats, ensuring your team stays prepared to handle evolving wireless security challenges.
Properly Dispose of Wireless Devices
Getting rid of wireless access points without proper precautions can leave sensitive data exposed to potential misuse.
The National Institute of Standards and Technology (NIST) estimates that up to 10% of data breaches stem from improperly discarded network devices. This concern was echoed in a 2022 Ponemon Institute study, which reported a 43% incident rate linked to lost or improperly disposed IT assets.
One notable example occurred in June 2021 when UCSF faced a data breach after a decommissioned access point was resold without its data being securely erased. This oversight exposed network credentials and led to the implementation of stricter disposal protocols.
Clear Configuration Settings
Simply performing a factory reset on a wireless access point doesn’t always guarantee complete removal of sensitive data. Configuration logs and other critical information stored in non-volatile memory can persist, even after a reset.
To ensure thorough data erasure, start with a factory reset, but don’t stop there. Use the management interface to manually delete any remaining credentials, configurations, or cached data. Enterprise-grade devices, in particular, often store sensitive information in multiple memory locations that standard resets may not address. Verification is key - review the device settings through its management interface and, when dealing with high-security environments, consider using diagnostic or forensic tools to confirm no residual data remains. In some cases, secure erasure procedures or multiple resets may be required to fully sanitize the device. Always refer to the manufacturer’s guidelines for model-specific instructions.
For organizations handling highly sensitive information, physical destruction of memory components, like shredding flash memory chips, may be necessary. While this approach is more costly, it provides the highest level of security.
| Disposal Method | Security Risk | Cost | Recommended For |
|---|---|---|---|
| Factory Reset Only | Medium | Low | Home/small business |
| Certified E-Waste | Low | Medium | Enterprise/regulatory use |
| Physical Destruction | Very Low | High | Highly sensitive data |
Document Device Removal
Keeping accurate records of decommissioned devices is essential for security audits, regulatory compliance, and preventing unauthorized reuse. Failing to document device removal can lead to inventory errors and increase the risk of rogue hardware being exploited.
When decommissioning a wireless access point, update your asset management system immediately. Record key details such as the device’s serial number, MAC address, removal date (in MM/DD/YYYY format), reason for decommissioning, and final disposition - whether it was recycled, destroyed, or donated. Include the technician’s name responsible for the erasure process and retain any certificates of destruction provided by disposal vendors.
Standards like NIST SP 800-88 (media sanitization) and regulations such as HIPAA or PCI DSS require secure data erasure and proper documentation to protect sensitive data and ensure compliance. Keep all disposal records in a secure location and have authorized personnel review and sign off on the process to establish accountability.
For organizations managing multiple sites, centralized documentation tools like BizBot can simplify tracking and automatically generate compliance reports. Automated asset management systems can also help by sending alerts for end-of-life devices, scheduling disposal tasks, and maintaining detailed records. Regular audits of your inventory can identify any gaps and confirm that all decommissioned devices are accounted for, supporting both security and compliance goals.
Disposing of devices securely is a critical final step in safeguarding your network, ensuring that outdated hardware doesn’t become a weak link.
Conclusion: Key Steps for Wireless Access Point Security
To keep your wireless access points secure, start by changing default settings, enforcing strong encryption standards, and conducting regular system checks. Protecting data in transit is equally important.
Use WPA2 with AES or WPA3 to ensure strong encryption. Make it a habit to perform firmware updates regularly to patch vulnerabilities and keep your devices secure.
Control physical access to your hardware and segment your network using VLANs and firewalls. This approach minimizes the damage if an attacker manages to breach your wireless network.
Ongoing monitoring is crucial. Tools like intrusion detection systems and regular scans for rogue access points can help you spot threats early. Combine this with robust credential management for an added layer of security.
Employee awareness plays a big role too. Train your team to identify wireless security risks and report unusual activity. Regular refresher training sessions can help keep everyone vigilant.
For organizations managing multiple locations, centralized management platforms - like BizBot - can simplify asset tracking and compliance. These tools help organize device deployment, maintenance, and decommissioning, keeping your security efforts streamlined.
FAQs
What are the best ways to secure my wireless access point if WPA3 encryption isn't available?
If WPA3 encryption isn't available, don't worry - there are still plenty of ways to secure your wireless network effectively:
- Stick with WPA2 encryption: It's not the latest, but WPA2 remains a solid and reliable security protocol that's widely supported.
- Update default settings: Change the default network name (SSID) and admin credentials to something unique and difficult to guess.
- Set a strong Wi-Fi password: Use a complex password that includes a mix of uppercase and lowercase letters, numbers, and special characters.
- Keep your router firmware up to date: Regularly check for firmware updates from your router's manufacturer to fix any potential security flaws.
- Turn off WPS: Wi-Fi Protected Setup (WPS) can leave your network vulnerable. Disabling it can add an extra layer of protection.
Taking these steps can go a long way in safeguarding your network from unauthorized access, even if WPA3 isn't an option.
What are the best practices for monitoring and addressing security threats on a wireless network?
To keep your wireless network safe, it's crucial to keep an eye on potential threats and address them promptly. Start by turning on the logging and monitoring features on your wireless access point. These tools help you track unusual activity or attempts at unauthorized access. Pair this with network monitoring tools to keep tabs on connected devices and spot any irregularities in real-time.
Make sure your access point's firmware is always up to date. Firmware updates often come with important security fixes that protect your network from new threats. Set up alerts to notify you about suspicious activities, like failed login attempts or unfamiliar devices trying to connect. Lastly, take the time to review your security settings and conduct regular audits. These steps can help you catch potential weaknesses before they turn into problems.
Why should I change the default SSID and password on my wireless access point, and how does it improve security?
Changing the default SSID (your network's name) and password on your wireless access point is a key step in keeping your network secure. Default settings are commonly known and can be an open invitation for hackers looking to exploit them for unauthorized access.
When you set up a unique SSID and pair it with a strong, custom password, you make your network much tougher to breach. This straightforward action adds an extra layer of protection, helping to keep your sensitive information safe from potential threats.